Blog Related
Your RFID Contactless Card Reader Truly Secure?
2025-08-18RFID Contactless Card Reader security starts with a hard question: is your device truly protecting people, payments, and identities - or just moving lines faster? As a manufacturer, Tianteng meets this question every day across banking, transit, access control, retail, and healthcare. Below, we share how vulnerabilities appear in real deployments, how we design against them, and how to roll out a reader with confidence.
The Risks You Don't See in an RFID Contactless Card Reader
When a tap just works, it's easy to assume it's safe. Yet the most common failures in a RFID Contactless Card Reader aren't dramatic breaches; they're quiet gaps that accumulate risk.
• Hidden Attack Surfaces and Operational Pitfalls
Integration is the first pressure point. Readers get added to legacy POS terminals, turnstiles, and kiosks with mixed firmware and inconsistent key management. Over time, default keys remain in place, test certificates slip into production, and audit logs aren't captured. That's how issues hide.
Back-end connections are a common weak spot. If the host doesn't enforce mutual authentication, a spoofed reader can pass as genuine. And even with encryption, poor key rotation leaves data open to replay and cloning.
Supply chain trust also matters. A RFID Contactless Card Reader can be strong on paper but unsafe in practice if it lacks tamper evidence or if firmware can be flashed without signature checks. Uncontrolled peripherals - USB injectors, debug pads left open inside housings - turn routine maintenance into an attack vector.
Finally, there's the business impact that isn't always labeled "security." Poor read performance and noisy RF environments push operators to relax timeouts or disable checks just to keep lines moving. That's where convenience quietly erodes assurance.
•Device spoofing through weak host authentication
•Static or default keys left in production
•Unsigned firmware and unsecured debug interfaces
•Over-permissive settings added to "fix" queue slowdowns
•Incomplete logs that break forensic visibility
How Tianteng Builds Security Into TTCE-R600
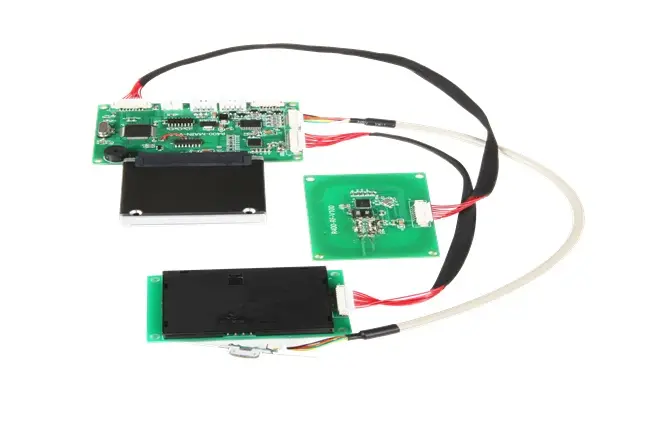
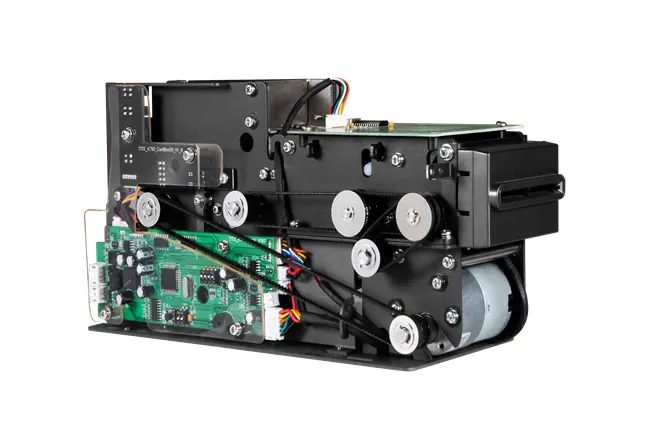
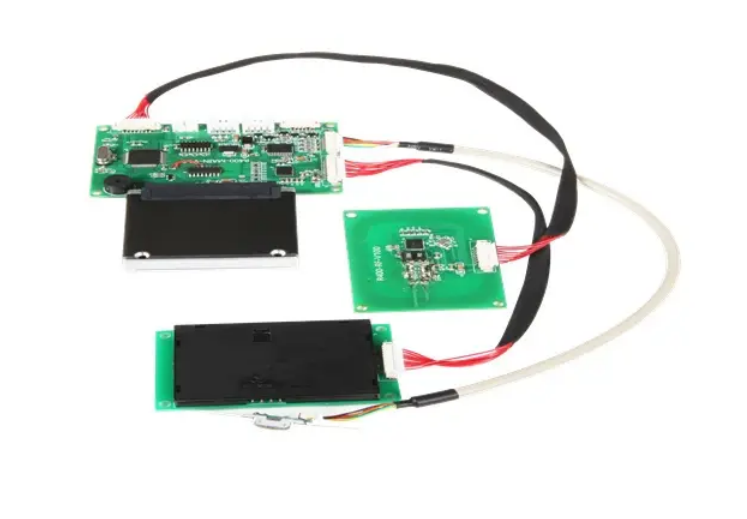
At Tianteng, we engineer from the module outward because real security starts in hardware, not in a policy document. Our TTCE-R600 is an embedded card reader module designed for secure, multi-form factor environments where reliability, performance, and lifecycle control matter.
• Security By Design, Not as An Add-on
TTCE-R600 supports IC/RFID card read/write and optional magnetic card read in one compact module. Multi-in-one flexibility means you can consolidate acceptance while maintaining strong controls. The module processes data in a tamper-resistant way, guarding secrets even if a device is opened.
It natively supports ISO/IEC 14443 Type A and Type B for contactless operation and works with MIFARE families such as Classic (S50/S70), Ultralight, Plus, and DESFire. For contact cards, it supports ISO 7816 with T=0/T=1 CPU cards, as well as PSAM for secure key storage and application security. This combination gives you robust authentication, flexible application selection, and tighter cryptographic hygiene across form factors.
Powered by USB, the module drops straight into kiosks, terminals, and gates. That means simpler wiring, fewer failure points, and consistent power delivery across your fleet. Its rugged, low-maintenance design keeps uptime high - without relaxing security just to keep operations moving.
• What this means in day-to-day deployments
Most sites must handle both legacy and modern credentials. With TTCE-R600, you can run contactless access control while keeping magnetic-stripe fallback where policy requires - under one auditable device profile. Firmware is update-ready for controlled, staged rollouts, helping teams standardize across locations without exposing the platform to unsigned images or unreviewed builds.
And because speed is part of safety, TTCE-R600 is tuned for fast, seamless transactions. Better read quality reduces retries and line anxiety, so teams don't resort to risky configuration shortcuts. In banking, that keeps ATM card issuance and payments crisp.Transit, it keeps gates flowing. In hotels and offices, it keeps access control responsive and reliable.
✅IC/RFID read/write plus optional magnetic read in one module
✅Secure, tamper-resistant data processing and PSAM support
✅USB power for simple, consistent integration
✅Fast transactions that protect user experience and security posture
✅Built for durability with minimal maintenance needs
Use cases include secure ATM workflows and payment processing, access control for offices and hotels, ticketing and fare collection in transport hubs, retail loyalty and membership verification, and patient identity and records access in healthcare. Each of these relies on the same foundation: strong authentication at the edge, controlled keys, and clean, repeatable integrations.

Choosing and Deploying the Right Reader, the Right Way
Selecting a RFID Contactless Card Reader is only half the job. The other half is deploying it with discipline. Here's the approach we advise - and build for - as your manufacturing partner.
• Practical Steps to Raise Your Security Baseline
Lock down identities end-to-end. Use PSAM for key storage and enforce mutual authentication between reader and host. Configure application selection for your environment so only intended card apps are accepted. Treat host connections as part of the attack surface and monitor them with the same care you give the device.
Standardize firmware and configuration profiles. Define a golden image for each site type and roll it out through a signed, traceable process. Keep logs - on the reader where applicable and on the host - so you can perform rapid forensics without guessing. And keep operations teams aligned: the best cryptography can't help if someone disables checks to fix a queue.
Design for RF realities. Gate arrays, POS counters, and hospital stations are noisy. Good antenna placement, controlled power, and realistic timeouts matter. TTCE-R600's performance headroom allows you to keep policies strict without sacrificing throughput.
Plan lifecycle from day one. Readers live in the field for years. Choose hardware that stays maintainable and secure without frequent site visits. With an embedded module like TTCE-R600, fleet upkeep stays simple: you get controlled updates, standardized parts, and a stable SDK and API layer that won't break between releases.
If you're defining requirements, two useful long-tail angles are "RFID access control reader security best practices" and "contactless payment terminal compliance." Use them to shape policy, test plans, and internal reviews so your deployment meets industry obligations while staying practical for front-line teams.
Call-to-Action: Lock down your edge and keep transactions fast. Pilot Tianteng's TTCE-R600 RFID Contactless Card Reader - risk assessment, integration plan, and a rollout tuned for performance and protection.