Blog Related
How an NFC Credit Card Reader Can Protect Customer Data
2025-11-20NFC Credit Card Reader security is not a feature you add later; it is the foundation customers notice first - even if they never see it. At TTCE, we build readers that turn a quick tap into a trusted, verifiable exchange. Below, we explain in simple terms how the right hardware, clean cryptography, and practical integration choices protect cardholder data while keeping checkout lines moving.

The First Security Check Happens At The Reader
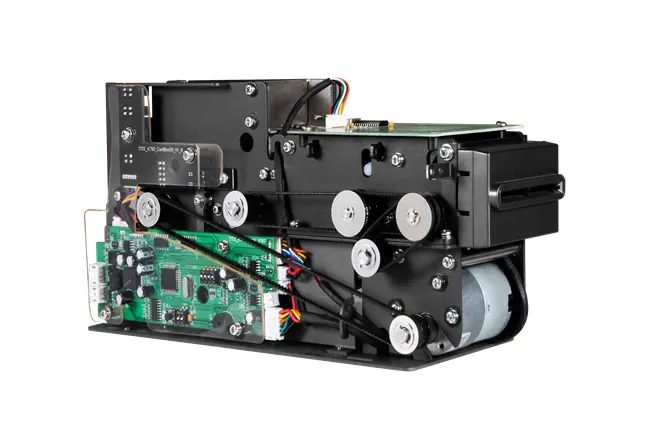
Most data-protection stories start in the cloud. Ours starts where a card meets a device. If the reader is slow, flaky, or easy to spoof, the rest of your stack spends all day playing catch-up. A modern NFC Credit Card Reader should do three things from the first millisecond: authenticate the card, encrypt sensitive elements, and resist tampering.
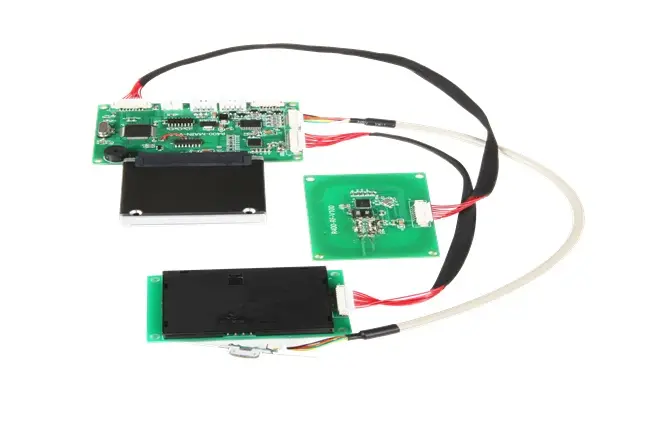
TTCE designs readers that support ISO/IEC 14443 Type A & Type B and well-known MIFARE families (S50, S70, Ultralight, Plus, DESFire). That broad compatibility matters for security, not just convenience. When a store can accept standard contactless cards reliably, staff don't fall back to manual key-entry or magstripe swipes - two paths where sensitive data is most exposed.
We also use two Secure Access Module (SAM) slots to keep cryptographic keys in dedicated hardware. Keys do not live in app code or general memory, so offline extraction gets much harder. Mutual authentication becomes routine: the reader proves itself to the card, the card proves itself to the reader, and your system stops trusting anything that cannot pass the handshake.
Speed plays a role too. Strong radio performance and quick anti-collision reduce retries. A "first-tap" approval keeps queues short and removes the temptation to override controls "just this once." Fewer workarounds mean fewer weak links.

Inside The Box: How TTCE Defends Each Tap
Security is not a single feature - it's a set of practical decisions that line up. Here's how a TTCE NFC Credit Card Reader keeps customer data safe without slowing your day.
Hardware Roots Of Trust
Our approach starts with a secure boot chain and signed firmware. Only trusted code runs on the device. If someone tampers with the unit, protections can lock access to secrets held in the SAMs, rendering any captured data useless to an attacker. This is the quiet work that customers never notice - but auditors do.
Standards That Prevent Shortcuts
By supporting ISO/IEC 14443 A/B and mainstream MIFARE cards, we keep authentication flows standardized. Transit gates, hotel doors, retail loyalty counters, and healthcare stations can use one reader family without bolting on custom "temporary fixes." Standard protocols mean vetted cryptography, predictable behavior, and easier compliance reviews.
Encrypt At Capture - Not After
The most common gap we see is "encryption later." Teams protect data in transit and at rest, but the content leaves the reader in the clear for a few inches of cable or a few hops of middleware. We design for encryption at the point of interaction. Sensitive elements are protected before they move across RS232 or USB, so sniffing a cable or scraping a host log yields nothing useful.
- Edge Encryption: Data is encrypted the moment it is read
- Mutual Authentication: Reader↔Card trust anchored by keys in SAM
- Key Isolation: Secrets live in hardware, not application code
- Protocol Alignment: ISO/IEC 14443 and MIFARE families supported
- Flexible Integration: RS232/USB connectivity without weakening security

Where This Matters Day To Day
In payments, better security reduces chargebacks and keeps checkout fast. Transit systems process taps at pace while limiting card cloning. Access-control points verify identities without exposing credentials to the network. Retail loyalty counters validate members and rewards without leaking profile data. Hospitals keep patient IDs accurate and private - even during rush hours. One reader family, the same security posture, consistent outcomes.
Choosing With Confidence: A Buyer's Shortlist
A secure NFC Credit Card Reader is only as strong as the integration around it. Use the checklist below to separate marketing fluff from real protection - and to align your team on what "good" looks like.
✅ Security-First Questions You Should Ask
- Where are the keys stored? Prefer SAM-backed storage and on-device cryptography.
- Is data encrypted at capture? Do not rely solely on host-side encryption or network TLS.
- Which card standards are supported? ISO/IEC 14443 A/B and core MIFARE families reduce custom, risky workarounds.
- How do we integrate? RS232 or USB is fine - if payloads stay encrypted and firmware updates are signed.
- What is the update path? Regular, verified updates close vulnerabilities without taking lanes offline.

✅ Reduce Friction Without Removing Controls
Security should feel invisible to shoppers and staff. TTCE's refined sensitivity, rapid collision avoidance, and steady RF ensure first-tap, every tap. When taps work the first time, no one is tempted to type card numbers, keep paper backups, or bypass procedures "until the line clears." Smooth flows are not just a UX victory; they are a risk-reduction strategy.
✅ Plan For Scale - And Fewer Surprises
Your security model should expand as your business grows. The same reader family can serve a POS lane today, a kiosk tomorrow, and an entry gate next quarter. With SAM-based keys, standards-driven protocols, and RS232/USB options, you avoid redesigning your controls for every new touchpoint. Teams stay trained. Audits stay simpler. Total cost stays predictable.
Why TTCE For Your Next Rollout
We build for the messy reality of retail counters, busy stations, and public spaces. That means durable housings, stable firmware, and clear integration guides for both legacy and modern systems. It also means we sweat the unglamorous details - error codes that help technicians, logs that help compliance teams, and update paths that avoid downtime. The result is a NFC Credit Card Reader that protects data at the edge and performs under pressure.
Call To Action
If you're ready to protect every tap without slowing your operation, talk to TTCE. We'll help you design encryption-at-capture, map key management with SAM modules, and integrate cleanly over RS232 or USB. Let's deploy a secure NFC Credit Card Reader where it counts most - right where your customers pay.