Blog Related
How to Detect ATM Card Writer Fraud in Time?
2025-08-20ATM card writer security is only as strong as your ability to spot anomalies early - and to act before they become losses. From Tianteng's perspective as a manufacturer, we see how subtle signals in hardware, firmware, and operations can flag fraud long before it reaches customers. In this guide, we share a practical, field-tested approach to how to detect ATM card writer fraud in time, and show how our TTCE-M800 motorized card reader helps close the gaps.

Why ATM Card Writer Fraud Goes Unnoticed
Fraudsters thrive in quiet corners of the workflow. Many teams focus on cash cassettes and network traffic but overlook the ATM card writer path. Attackers target that path because it touches real cards, real identities, and real value. We see three recurring stress points across banks, OEMs, and service providers: First, loose or misaligned bezels make device surfaces easy to tamper with; a thin shim or hidden overlay can divert, block, or harvest card data. Second, firmware is often treated as "set and forget." Without routine integrity checks, a brief access window is enough for an attacker to sideload malicious code. Third, logs are abundant but noisy, so critical alerts get buried in everyday operational chatter.
• Early Warning Signs at the Device Level
You can often spot trouble with simple, consistent checks. Focus on tangible clues that a technician can confirm in minutes:
✅Unusual card friction on entry or exit, or minor misalignment at the slot
✅Scratches, scuffs, or new residue around the bezel - signs of an overlay attempt
✅Unexpected reboots or "safe mode" behavior after doors open or power cycles
✅Sudden increases in rejected writes or fallback to magnetic-only processing
✅New, unrecognized accessories near the slot (tiny boards, thin cables, or "cleaners")
✅Any tool marks around fasteners that were not present during the last service
Small signals build a larger story. If two or three of these appear together, pause service and escalate. Quick isolation prevents data theft and protects brand trust.
A Practical Detection Playbook for Banks and Operators
You do not need complex analytics to start strong. Blend simple routines with a few decisive controls. Keep it light, repeatable, and auditable so teams actually use it.
• Daily Monitoring Checklist
Build a quick, repeatable daily routine that frontline staff can complete in minutes - ideally tied to shift handovers or cash reloads - by inspecting the ATM card writer slot for gaps, wobble, misalignment, or foreign objects; power-cycling to confirm a normal boot flow with no odd prompts; running a write test with a known-good card and noting any new noise, drag, or hesitation; verifying the firmware version against your approved whitelist; checking PSAM presence, seal integrity, and serials (if used); and capturing a log snapshot to spot anomalies such as repeated write fallbacks, unusual retries, or timed bursts. A few minutes each day can prevent months of headaches. If an alert fires, keep the response crisp and controlled: quarantine the terminal, notify your incident channel, swap the reader with a sealed spare, photograph the bezel, fasteners, and internal harnessing, and export the last 24 hours of card-path logs along with the firmware hash - aiming for rapid containment and clean forensics with no guesswork.
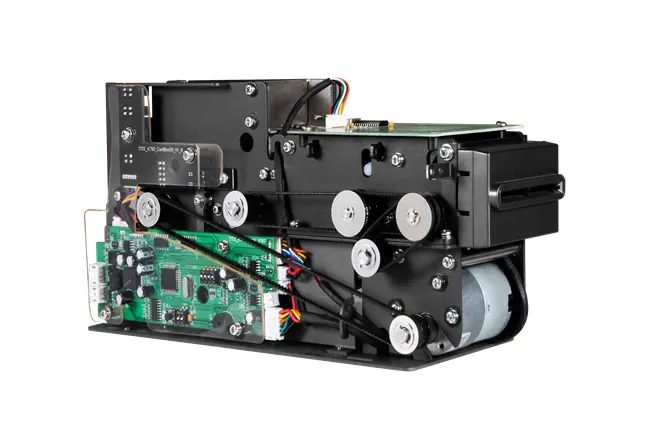
• TTCE-M800: Design That Makes Fraud Hard
At Tianteng, we build security into the path where risk lives: the card slot, the movement rails, and the logic that governs read/write. Our Credit Card Reader Writer TTCE-M800 is a motorized card reader engineered to strengthen detection and reduce tampering windows while keeping service simple. Comprehensive card support, fewer blind spots. TTCE-M800 reads and writes magnetic, IC, and RFID/contactless cards. This full-spectrum capability removes fragile workarounds and ensures your system does not fall back to a weaker mode during an attack. It also means operators have a single, consistent inspection routine across card types.

Engineered slot protection. A dust- and foreign-object-resistant bezel helps block shims and debris that attackers use to manipulate card travel. Stable alignment reduces false friction signals, so when the device does feel different, your team treats it as a real anomaly. The motorized path supports power-down eject, preventing card capture during forced shutdowns - a classic tactic to keep victims at the terminal while criminals act nearby. Built for secure ecosystems. TTCE-M800 is compatible with common communication protocols and supports PSAM options to anchor cryptographic operations to dedicated secure modules. This creates a strong trust boundary for write operations and makes EMV and PBOC compliance workflows smoother. In practice, it means your rules for what can be written, when, and by whom stay enforceable in the field.
Durable mechanics, precise movement. The card channel uses composite materials designed for heat and wear resistance, with stainless-steel guidance to maintain precision over time. Consistent mechanics produce consistent telemetry - noise, retries, and timing behavior stay stable - so your monitoring can flag variance more reliably. Robust electrical design includes multiple protection functions to safeguard against unsafe power conditions that attackers sometimes simulate to force erratic behavior. Modular design for fast service. Fraud wins when downtime is long. TTCE-M800's modular structure makes removal and replacement straightforward. Technicians can swap a reader module quickly and send it for analysis without leaving a terminal exposed. Fewer tools, fewer steps, less risk.
• Configuration Tips for Fraud Detection
A secure device becomes a smarter sensor when you configure it with operations in mind. Here is how we recommend deploying a EMV-compliant ATM card writer like the M800:
✅Enable firmware whitelisting and lock updates to signed packages only
✅Use PSAM for key storage and transactional checks on write operations
✅Log card-path states at a human-readable level; train staff on a five-line daily review
✅Pair the bezel with tamper-evident seals and document their positioning with photos
✅Define a "golden feel" procedure: one test card, same insertion speed, same notes each shift
✅Keep a sealed spare reader on site to enable immediate quarantine and swap
These practices are small by design. They fit into real maintenance windows and scale across large fleets.
Why Tianteng?
We approach ATM card writer security as a lifecycle, not a single feature. From design reviews to pilot deployments, our engineers help you translate policy into repeatable actions at the device edge. The outcome is early detection, faster recovery, and fewer surprises.
Call-to-Action: If you are rethinking ATM card writer fraud detection, ask us for a hands-on demo of the TTCE-M800 and a short deployment checklist tailored to your environment. Our team can walk your technicians through daily checks, recommend PSAM configurations, and show how the M800's modular design accelerates incident response. Contact Tianteng today to turn your card path into a reliable line of defense - before attackers get a foothold.